Combating Information Manipulation: A Playbook for Elections and Beyond | International Republican Institute

The Gas Siphon Attack: The Technical and Economic Realities Behind Hacking Exchanges · Devcon Archive: Ethereum Developer Conference
wp-k8s: WordPress on Kubernetes project (GKE, cloud SQL, NFS, cluster autoscaling, HPA, VPA, Ingress, Let's Encrypt) - FoolControl: Phear the penguin
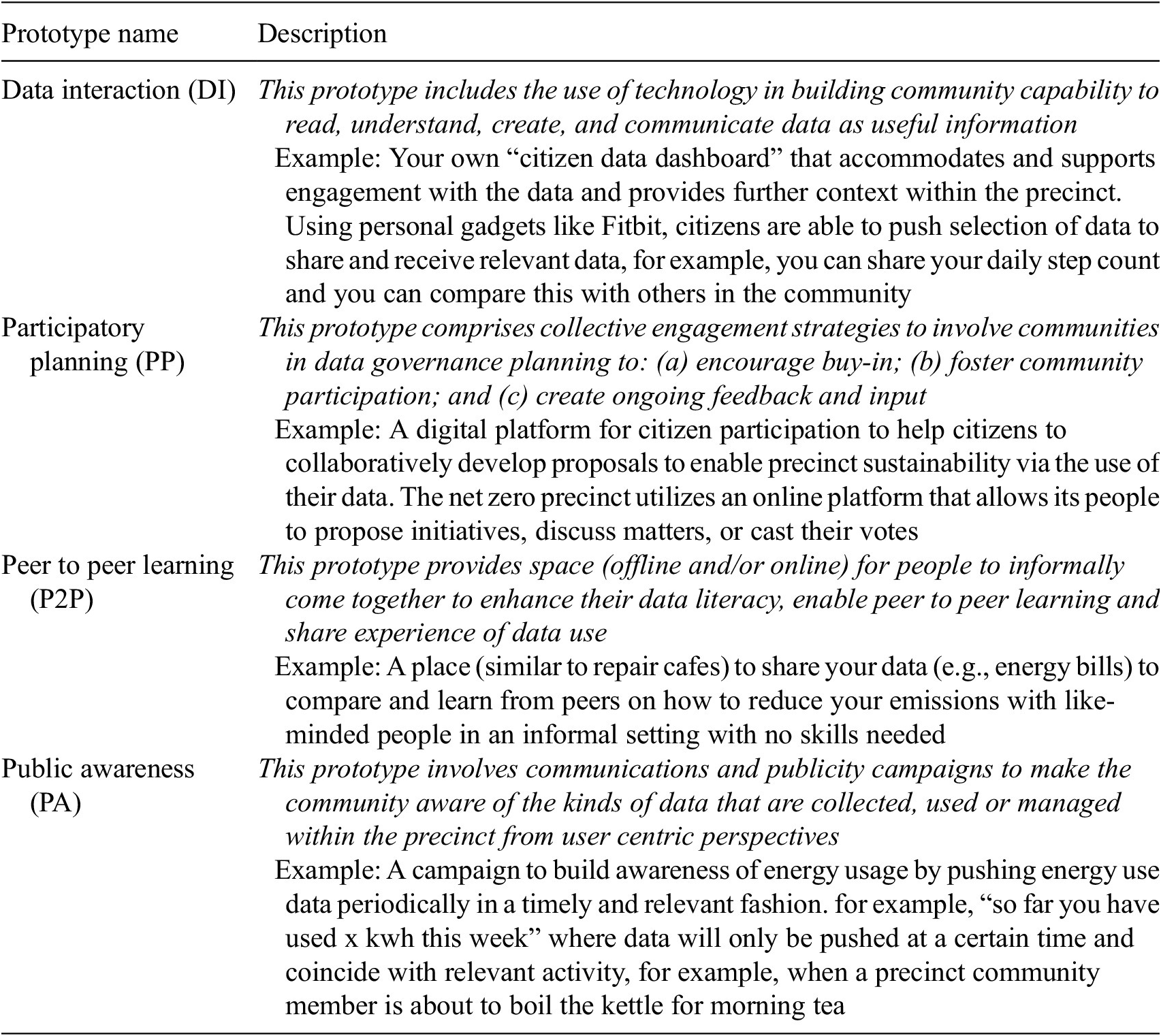
A participatory approach for empowering community engagement in data governance: The Monash Net Zero Precinct | Data & Policy | Cambridge Core







![Exploitation] D-Link DAP-1860 Vulnerability | by Infiniti Team | Medium Exploitation] D-Link DAP-1860 Vulnerability | by Infiniti Team | Medium](https://miro.medium.com/v2/resize:fit:1400/0*6Cs6yeRlMB6wIozc.png)
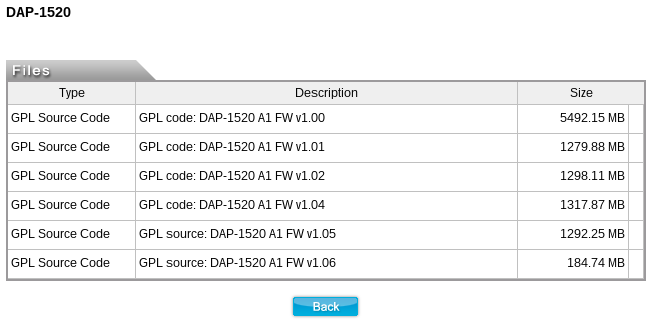

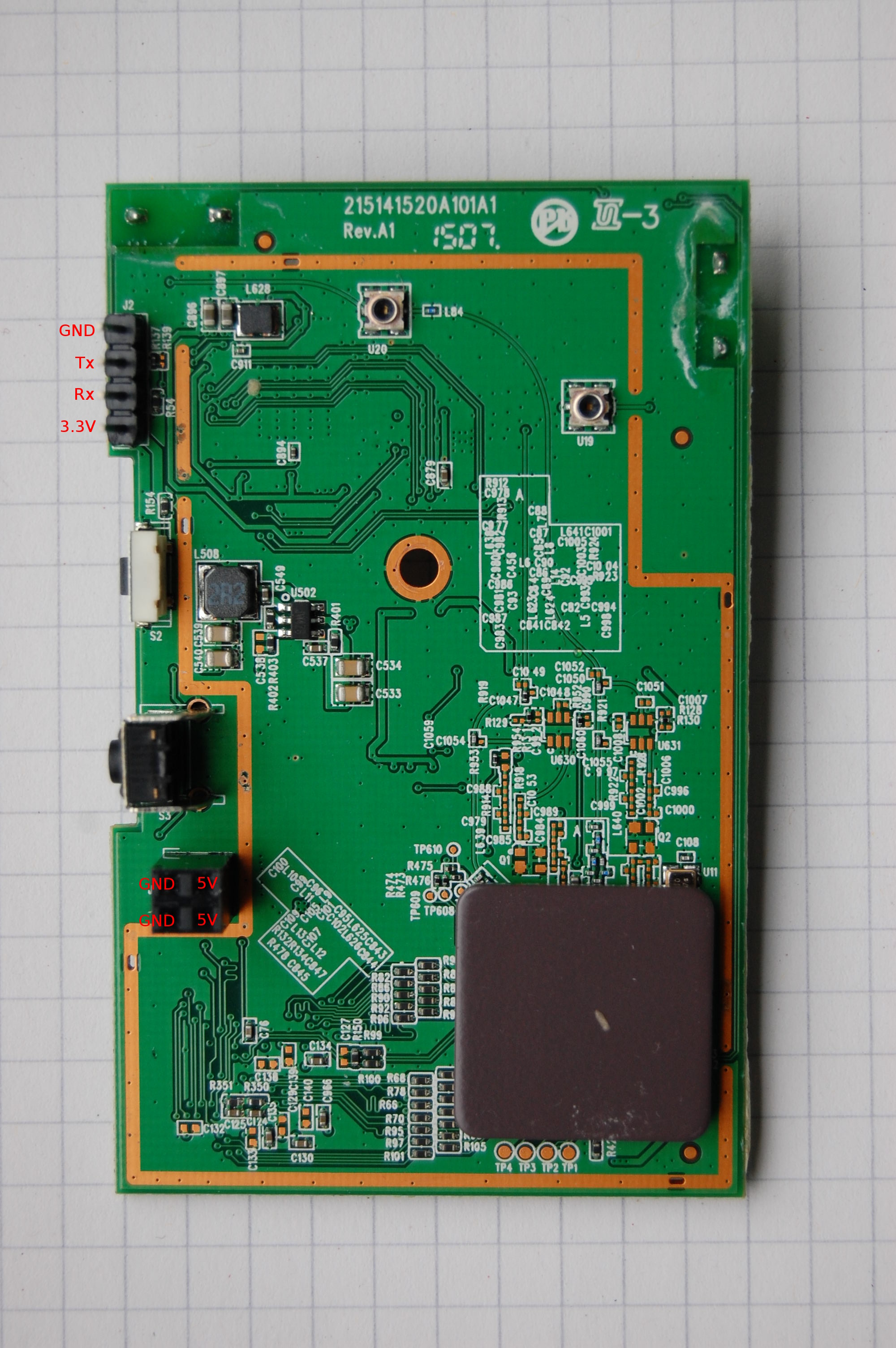

![Exploitation] D-Link DAP-1860 Vulnerability | by Infiniti Team | Medium Exploitation] D-Link DAP-1860 Vulnerability | by Infiniti Team | Medium](https://miro.medium.com/v2/resize:fit:988/0*R4W3w1UlpAdzrNbA.png)